How data exchange occurs over a local network. Setting up shared folder access over a network in Windows
Methods of data exchange in local networks
To control the exchange (network access control, network arbitration), various methods are used, the features of which largely depend on the network topology.
There are several groups of access methods based on time division of the channel:
centralized and decentralized
deterministic and random
Centralized access is controlled from a network control center, such as a server. The decentralized access method operates on the basis of protocols without control actions from the center.
Deterministic access provides each workstation with a guaranteed access time (for example, scheduled access time) to the data transmission medium. Random access is based on the equality of all stations in the network and their ability to access the medium at any time to transmit data.
Centralized access to mono channel
In networks with centralized access, two access methods are used: the polling method and the delegation method. These methods are used in networks with an explicit control center.
Survey method.
Data exchange on a LAN with a star topology with an active center (central server). With a given topology, all stations can decide to transmit information to the server at the same time. The central server can communicate with only one workstation. Therefore, at any time it is necessary to select only one station broadcasting.
The central server sends requests to all stations in turn. Each workstation that wants to transmit data (the first one polled) sends a response or immediately begins transmission. After the end of the transmission session, the central server continues polling in a circle. Stations, in this case, have the following priorities: the maximum priority is for the one that is closest to the last station that completed the exchange.
Data exchange in a network with a bus topology. This topology may have the same centralized control as a star. One of the nodes (the central one) sends requests to all the others, finding out who wants to transmit, and then allows the transmission to whichever one of them reports it after the end of the transmission.
Transfer of authority method (passing token)
A token is a service package of a certain format into which clients can place their information packages. The sequence of transmitting a token over the network from one workstation to another is set by the server. The workstation receives permission to access the data transmission medium when it receives a special token packet. This access method for networks with bus and star topologies is provided by the ArcNet protocol.
Decentralized access to mono channel
Let's consider decentralized deterministic and random methods of access to the data transmission medium.
The decentralized deterministic method includes the token passing method. The token passing method uses a packet called a token. A token is a packet that does not have an address and circulates freely over the network; it can be free or busy.
Data exchange in a network with a ring topology
1. This network uses the “token passing” access method. The transfer algorithm is as follows:
a) a node wishing to transmit waits for a free token, upon receiving which it marks it as busy (changes the corresponding bits), adds its own packet to it and sends the result further into the ring;
b) each node that receives such a token accepts it and checks whether the packet is addressed to it;
c) if the packet is addressed to this node, then the node sets a specially allocated acknowledgment bit in the token and sends the modified token with the packet further;
d) the transmitting node receives back its message, which has passed through the entire ring, releases the token (marks it as free) and again sends the token to the network. In this case, the sending node knows whether its package was received or not.
For the normal functioning of this network, it is necessary that one of the computers or a special device ensure that the token is not lost, and if the token is lost, this computer must create it and launch it into the network.
Data exchange in a network with bus topology
In this case, all nodes have equal access to the network and the decision when to transmit is made by each node locally, based on an analysis of the network state. Competition arises between nodes for network capture, and, therefore, conflicts between them are possible, as well as distortion of transmitted data due to packet overlap.
Let's look at the most commonly used carrier sense multiple access with collision detection (CSMA/CD). The essence of the algorithm is as follows:
1) a node that wants to transmit information monitors the state of the network, and as soon as it is free, it begins transmission;
2) the node transmits data and simultaneously monitors the state of the network (carrier sensing and collision detection). If no collisions are detected, the transfer is completed;
3) if a collision is detected, the node amplifies it (transmits for some more time) to ensure detection by all transmitting nodes, and then stops transmitting. Other transmitting nodes do the same;
4) after the unsuccessful attempt is terminated, the node waits for a randomly selected period of time tback, and then repeats its attempt to transmit, while controlling collisions.
In case of a second collision, trear increases. Eventually, one of the nodes gets ahead of the other nodes and successfully transmits the data. The CSMA/CD method is often called the race method. This method for networks with a bus topology is implemented by the Ethernet protocol.
graduate work
1.9 Methods of data exchange in local networks
To control the exchange (network access control, network arbitration), various methods are used, the features of which largely depend on the network topology.
There are several groups of access methods based on time division of the channel:
centralized and decentralized
deterministic and random
Centralized access is controlled from a network control center, such as a server. The decentralized access method operates on the basis of protocols without control actions from the center.
Deterministic access provides each workstation with a guaranteed access time (for example, scheduled access time) to the data transmission medium. Random access is based on the equality of all stations in the network and their ability to access the medium at any time to transmit data.
Centralized access to mono channel
In networks with centralized access, two access methods are used: the polling method and the delegation method. These methods are used in networks with an explicit control center.
Survey method.
Data exchange on a LAN with a star topology with an active center (central server). With a given topology, all stations can decide to transmit information to the server at the same time. The central server can communicate with only one workstation. Therefore, at any time it is necessary to select only one station broadcasting.
The central server sends requests to all stations in turn. Each workstation that wants to transmit data (the first one polled) sends a response or immediately begins transmission. After the end of the transmission session, the central server continues polling in a circle. Stations, in this case, have the following priorities: the maximum priority is for the one that is closest to the last station that completed the exchange.
Data exchange in a network with a bus topology. In this topology, perhaps the same centralized control as in the "star". One of the nodes (the central one) sends requests to all the others, finding out who wants to transmit, and then allows the transmission to whichever one of them, after the end of the transmission, reports it .
Transfer of authority method (passing token)
A token is a service package of a certain format into which clients can place their information packages. The sequence of transmitting a token over the network from one workstation to another is set by the server. The workstation receives permission to access the data transmission medium when it receives a special token packet. This access method for networks with bus and star topologies is provided by the ArcNet protocol.
Decentralized access to mono channel.
Let's consider decentralized deterministic and random methods of access to the data transmission medium. The decentralized deterministic method includes the token passing method. The token passing method uses a packet called a token. A token is a packet that does not have an address and circulates freely over the network; it can be free or busy.
Data exchange in a network with a ring topology (decentralized deterministic access method)
1. This network uses the “token passing” access method. The transmission algorithm is as follows:
a) a node wishing to transmit waits for a free token, upon receiving which it marks it as busy (changes the corresponding bits), adds its own packet to it and sends the result further into the ring;
b) each node that receives such a token accepts it and checks whether the packet is addressed to it;
c) if the packet is addressed to this node, then the node sets a specially allocated acknowledgment bit in the token and sends the modified token with the packet further;
d) the transmitting node receives back its message, which has passed through the entire ring, releases the token (marks it as free) and again sends the token to the network. In this case, the sending node knows whether its package was received or not.
For the normal functioning of this network, it is necessary that one of the computers or a special device ensure that the token is not lost, and if the token is lost, this computer must create it and launch it into the network.
Data exchange in a network with a bus topology (decentralized random access method)
In this case, all nodes have equal access to the network and the decision when to transmit is made by each node locally, based on an analysis of the network state. Competition arises between nodes for network capture, and, therefore, conflicts between them are possible, as well as distortion of transmitted data due to packet overlap.
Let's look at the most commonly used carrier sense multiple access with collision detection (CSMA/CD). The essence of the algorithm is as follows:
1) a node that wants to transmit information monitors the state of the network, and as soon as it is free, it begins transmission;
2) the node transmits data and simultaneously monitors the state of the network (carrier sensing and collision detection). If no collisions are detected, the transfer is completed;
3) if a collision is detected, the node amplifies it (transmits for some more time) to ensure detection by all transmitting nodes, and then stops transmitting. Other transmitting nodes do the same;
4) after the unsuccessful attempt is terminated, the node waits for a randomly selected period of time tback, and then repeats its attempt to transmit, while controlling collisions.
In case of a second collision, trear increases. Eventually, one of the nodes gets ahead of the other nodes and successfully transmits the data. The CSMA/CD method is often called the race method. This method for networks with a bus topology is implemented by the Ethernet protocol.
Automation of library processes
Data entry is carried out through the Edit component, data about contact persons is saved at the user's choice, a file is created with the extension ***...
Information system "Cultural and entertainment institutions of the city of Krasnoyarsk"
Figure 1 - Diagram of information flows in the program "KRU of the city of Krasnoyarsk" The main elements of the information system "Cultural and entertainment institutions of the city of Krasnoyarsk" are the Database "Cultural and entertainment institutions"...
Card file of enterprise department employees
In the FoxPro DBMS, it is possible to exchange data between individual source code files, between procedures of subroutines and functions in a procedural file, and between object components of a project...
Configurations of local networks and methods of switching between them
Transferring data to the CS involves organizing a physical or logical connection between interacting network subscribers (they are also called end nodes). These subscribers can be remote computers, local networks...
Local computer networks
Software and analytical complex for local network in the organization "Severodonetsk Community Development Agency"
To ensure consistent operation in data networks, various data communication protocols are used - sets of rules...
Protocols in local and global networks
A very important point is taking into account the factors influencing the choice of the physical transmission medium (cable system). Among them are the following: Required bandwidth...
Development of an autonomous hardware and software complex for the control subsystem of the "Dosimetrist Robot"
When developing algorithms for a protocol for guaranteed delivery of messages over a radio channel, we considered the algorithms of the TCP Transmission Control Protocol (TCP) - one of the main Internet network protocols...
Development of a virtual computer network
The purpose of a VPN is to provide users with a secure connection to an internal network from outside its perimeter, for example through an Internet service provider. The main advantage of a VPN is that as long as the software supports it...
Development of a project for protecting the local computer network of an educational institution
Local area network (LAN; English Local Area Network, LAN) is a computer network that usually covers a relatively small area or a small group of buildings (home, office, company, institute). There are also local networks...
Network software. Setting up local computer networks
To ensure consistent operation in data networks, various data communication protocols are used - sets of rules...
Database creation
Internal data exchange is carried out using variables. Variables can be passed to procedures and functions in three ways: By reference. The address of the variable is passed, which allows you to change its value. Used By Ref...
Structure and functions of LKS software
A local network can be applied to more than just the sharing of files or printers. There are also other, no less important applications. Very often, a local network is used for shared access to a database...
Local networks based on the IPv4 protocol may use special addresses assigned by the IANA (RFC 1918 and RFC 1597 standards): § 10.0.0.0-10.255.255.255; § 172.16.0.0-172.31.255.255; § 192.168.0.0-192.168.255.255. Such addresses are called private, internal...
School local network: setup and support
Different networks use different network protocols (data transfer protocols) to exchange data between workstations...
In the Windows operating system, you can connect shared access to a folder on a local home network to exchange data between computers using shared folders. This is a very convenient and fast way to transfer files computer-to-computer, without using external media (flash drives, external hard drives, memory cards, etc.).
In this article I will talk about creating a local network using the Windows 10 operating system as an example. Creating and setting up a local network in Windows 8 and Windows 7 is done in a similar way; these instructions are universal.
The article discusses the following option for using shared folders on a local network: several computers are connected to the router, connected via cable and wireless Wi-Fi network, united into a home network. A shared folder is created on each computer; all computers included in this local network have access to the shared folders.
On computers connected to the home local network, the operating systems Windows 10, Windows 8, Windows 7 (different OS, or the same operating system) can be installed, connected to the router via Wi-Fi or cable.
Creating and configuring a local network takes place in four stages:
- the first stage is checking the workgroup name and network card settings
- second stage - creating and configuring local network parameters
- third stage - connecting shared access to a folder on the local network
- fourth stage - data exchange over the local network
First you need to check the workgroup settings and network card settings, and then create a local Windows network.
Checking network card and workgroup settings
On the Desktop, right-click on the “This PC” icon (“My Computer”, “Computer”), select “Properties” from the context menu. In the “System” window, click on “Advanced system settings”.
In the “System Properties” window that opens, open the “Computer name” tab. Here you will see the workgroup name. By default, in Windows 10, a workgroup is named "WORKGROUP".
On all computers connected to this local network, the workgroup name must be the same. If the workgroups have different names on the computers you connect to the network, change the names by choosing one name for the workgroup.
To do this, click on the “Change...” button, in the “Changing computer or domain name” window, give a different name for the workgroup (write the new name in capital letters, preferably in English).
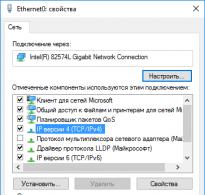
Now check your network card settings. To do this, in the notification area, right-click on the network icon (Internet access). Click on "Network and Sharing Center". In the Network and Sharing Center window, click the Change adapter settings link.
In the Network Connections window, select a network card, Ethernet or Wi-Fi, depending on how your computer connects to the Internet. Next, right-click on the network card and click on “Properties” in the context menu.
In the network card properties window, in the “Network” tab, select the “IP version 4 (TCP/IPv4)” component, and then click on the “Properties” button.

In the Internet Protocol Properties window that opens, in the “General” tab, check the IP address and DNS service settings. In most cases, these parameters are assigned automatically. If these parameters are inserted manually, check the corresponding addresses with your Internet provider (the IP address on computers connected to the network must be different).

After checking the settings, you can proceed directly to creating a local network in Windows.
Creating a local network
First of all, configure the local network settings in Windows. Enter the “Network and Sharing Center”, click on the “Change advanced sharing settings” item.
The Advanced Sharing Settings window allows you to change sharing settings for different network profiles. The Windows operating system creates a separate network profile with its own special parameters for each network used.
There are three network profiles available:
- Private
- Guest or public
- All networks
In your private network profile, under Network Discovery, select Enable Network Discovery.
In the File and Printer Sharing option, enable the Enable File and Printer Sharing option.
In the HomeGroup Connection option, select Let Windows manage HomeGroup connections (recommended).

After that, open the “All Networks” network profile. In the Public Folder Sharing option, select Enable sharing to allow network users to read and write files in public folders.
In the File Sharing Connection option, select the Use 128-bit encryption to secure sharing connections (recommended) option.
In the “Password Protected Sharing” option, enable the “Turn off Password Protected Sharing” option.

After completing the settings, click on the “Save Changes” button.
Repeat all these steps on all computers that you plan to connect to your home local network:
- check the workgroup name (name must be the same)
- check your network card settings
- In sharing settings, enable network discovery, enable file and printer sharing, disable password protected sharing
How to enable folder sharing
In this case, I created a folder named “General”. Right-click on this folder and in the folder properties window, open the “Access” tab.
Then click on the “Advanced setup” button.

In the “Advanced sharing settings” window, activate the “Share this folder” option, and then click on the “Permissions” button.

Select permissions to use shared folder data from another computer. There are three options to choose from:
- Full access
- Change
- Reading

To save the settings, click on the “OK” button.
Go back to the folder properties, open the “Security” tab, and then click on the “Change...” button.

In the window that opens, enter the name “Everyone” (without quotes) in the “Enter names of selected objects” field, and then click on the “OK” button.

In the folder properties window, in the “Security” tab, configure the permissions that you previously selected for the shared folder.

To change the permission for the “Everyone” group, click on the “Advanced” button. In the “Advanced security settings for a shared folder” window, select the “Everyone” group, and then click on the “Change” button to change permissions.
Setting up a local network in Windows is complete. In some cases, you may need to restart your computer for all changes to take effect.
Logging into your local home network
Open Explorer, in the “Network” section you will see all available computers connected to your local home network. To log into another computer, click on the computer name, and then click on the shared folder name to access the files and folders located in the shared folder.

The local network in Windows 10 has been created and configured.
Troubleshoot some network problems
Sometimes, after setting up the network, problems arise with accessing folders on the local network. One possible problem may be an incorrectly selected network profile. I encountered this myself on my computer. After reinstalling the system, I created and configured a local network, but my computer did not see two laptops connected to this network. From the laptop I could easily access the shared folder on my computer, but the computer did not see them at all.
I checked all the local network settings several times, and only then I noticed that my computer was running a public network, and not a private (home) network, like on laptops. How can such a problem be solved?
Enter the “Network and Sharing Center”, click on “Troubleshooting”. Select the “Shared Folders” section and run diagnostics and troubleshooting. At the very end, the application will offer to configure the network as private. Apply this fix, and then restart your computer. After performing this operation, my computer gained access to shared folders on laptops on the local network.
Often problems arise due to incorrect network configuration. Windows 10 has the option to reset network settings to default settings. Go to “Settings”, “Network and Internet”, in the “Change network settings” section, click on “Reset network” to apply the default network settings.
Other problems may arise; look for solutions on the Internet.
Conclusions of the article
In Windows OS, you can create a local private (home) network between computers, organize data exchange using shared folders, and gain access to a printer. Computers on the same network can have different or the same operating systems installed (Windows 10, Windows 8, Windows 7).
You probably have a wide variety of devices on your home network, be it Windows or Linux computers, Macbooks, or Android phones. And you'll most likely want to transfer files between them. Instead of copying files onto flash drives and running from room to room, it is much more convenient to simply set up shared folders on the local network. This is not difficult to do.
Windows
First of all, let's enable the ability to share files over the local network in the settings. Open Control Panel and go to Network and Internet → Sharing Options. Select the network you are connected to and enable the “Turn on network discovery” and “Turn on file and printer sharing” options.
Now right-click on the folder you want to share and select Options. In the folder options, on the “Sharing” tab, set access settings, allowing all users on your local network the ability to write and read files in the shared folder.
To view folders open on your local network, in Explorer, select Network in the sidebar.
macOS

Go to System Preferences on your Mac and select Sharing. Turn on File and Folder Sharing. Go to “Options...” and check “File and folder sharing via SMB.”
Below, in the “Shared Folders” section, you can choose which folders to share. If you want local network users to be able to upload files to these folders, in the Users section, grant read-write access to all users.
To access local network files, select Go from your Finder's menu bar and click Network.
Linux

Sharing folders in Linux is very easy. Let's take Ubuntu as an example.
Sharing Linux folders on the local network is provided by Samba. You can install it using the following command:
sudo apt-get install samba samba-common system-config-samba
In the file manager, right-click on the folder you want to provide access to from the local network. Open the folder's properties, go to the "Local Network Public Folder" tab and select "Publish this folder."
To be able to copy files to this folder from another computer, select Allow other users to change the contents of this folder.
If you do not want to enter your username and password again, check the “Guest access” checkbox.
You can access folders on your local network in Ubuntu by selecting Network in the sidebar of the Nautilus file manager.
iOS
You can connect to shared folders on your local network in iOS using FileExporer Free. Click the "+" button and choose which device you want to connect to: Windows, macOS or Linux. After searching for devices on your local network, FileExporer Free will provide you with a list of shared folders.
Any network interaction on a LAN is based on connecting computers using a cable system (CS). CS implementation options can be different even with the same network operating technology. Ethernet LANs of 10 Base standards operate on bus technology using the CSMA/CD random access method to the common transmission medium. This operating principle can be implemented using various topologies (Fig. 1, 2). In Fig. Figure 1 shows a traditional bus topology in which the network cards (network adapters) of all nodes using transceivers (transceivers) are connected to a cable system common to all nodes. Thus, the network is configured on two types of coaxial cable: “thick” and “thin” Ethernet
(10Base-5 and 10Base-2 standards).
In the 10Base-T and 10Base-F standards, each of the nodes (Fig. 2) is connected to one of the ports of the multiport repeater - hub Hub (hub), the operation of which is based on the principle: the hub transmits a signal received on one of the ports to the outputs of all ports of the hub, with the exception of the port on which this signal was received. The connection is made using twisted pairs (10Base-T) or fiber optic cable (10Base-F). By the nature of the connection, this type of LAN is physically implemented as a “star”, and according to the hub operation algorithm, it retains all the features of the bus topology.
 |
Similarly, the Token Ring network, which uses token ring technology, is physically configured as a star. The principle of concentrating some of the inter-node connections in the internal structure of the hub can be developed in order to achieve higher performance through parallel processing of intra-network traffic by connecting node segments to ports switch Switch (switch), but for now this is used in the logical structuring of the network.
Data exchange over the Ethernet network occurs in compliance with the following frame format:
|
Preamble |
Addressrecipient |
Address sender |
Field length data |
Data field |
|
|
46-1800 bytes |
The preamble is a kind of synchronization signal, during 7 bytes of which a sequence of alternating 1s and 0s is transmitted, which ends (in the eighth byte) with the initial frame delimiter 1010101 1 . After the preamble, the receiver is ready to analyze the message recipient address.
The recipient and sender addresses are unique addresses for each of the network cards, specified by the manufacturer. These are the so-called physical addresses. The location of these addresses at the beginning of the frame convinces us that it is simply necessary to know them, regardless of the location of the recipient and sender in the overall distributed internetwork structure.
CRC – field for protecting information with a cyclic code.
Generally speaking, physical addresses might be enough for exchange within a small isolated network, but they are completely insufficient for organizing a session between nodes located on different subnets. This happens for the simple reason that it is impossible to track billions of adapter addresses, the composition of which changes dynamically due to the addition of new nodes to the network or the exclusion of any part of them, replacement of network equipment, etc.
 |
Therefore, addressing nodes, regardless of their location, is performed according to a standard procedure, when each node, in addition to a physical address, is assigned another network an address that uniquely identifies both the network in which each node is located and the address of the node itself in this network. Since the IP network layer protocol is responsible for determining the message delivery route in the TCP/IP protocol stack, this address is often called the IP address and is placed in the header of this protocol (Fig. 3).
Thus, in accordance with the physical address, each of the adapters decides whether or not to accept the signal acting at its input, and the IP address simply determines the location of the required network node.
Since the IP address of the message recipient is initially known (or can be determined through the domain name service DNS), and the physical address must be determined, the network software provides a standard procedure for broadcasting an ARP request, the meaning of which means: “The host with such and such an IP address! Please provide your physical address." Although there are other means, such as storing some collections of addresses in a cache and then retrieving them when needed, determining a physical address (called hardware address resolution) via a broadcast request is universal.
Structure and classesIP addresses
First of all, an IP address is not the address of a computer, but its network card. Therefore, if a computer has several network cards, then it has the same number of IP addresses (Fig. 4).
 Rice. 4
Rice. 4
The IP address currently consists of 4 bytes, and this 32-bit binary combination can be written in different ways, for example:
In binary: 10000110 00011000 00001000 01000010;
In decimal: 2249721922;
In hexadecimal: Ох86180842;
In dotted decimal: 134.24.8.66.
Due to greater ease of perception, it is customary to write the IP address in the form: decimal with a dot.
In its structure, it consists of two parts: the network identifier (number) and the node identifier occupying the right (lower) part of the address. To be able to rationally distribute address space among existing networks of various sizes, an address classification system is used. As can be seen from the table, class A is provided for numbering a relatively small number of very large networks (N max = 127), each of which contains up to M max = 16,777,216 nodes. The zero value of the most significant bit of the network identifier determines membership in class A.
|
Class |
Elder bits |
IP- address |
Identifiernetworks |
Identifier node |
|
For broadcasting |
||||
Similarly, class B contains up to N max = 16,384 networks with the number of nodes in each up to M max = 65,536, and class C includes N max = 2,097,152 networks with M max< 256 узлов.
By determining the decimal value of the high byte of the network identifier, you can determine the membership of a specific class by IP address.
Network class |
Range of high byte values |
|
From 128 to 191 |
|
|
From 192 to 224 |
|
|
From 225 to 240 |
Additional conventions regarding the use of IP addresses are taken into account here:
If the network ID consists of all zeros, this means that the destination and origin nodes are on the same network;